Give firewalls the attention it deserves
Firewalls have always been the basic building blocks of network security. Its number continues to rise in organizations and 94 % of FireMon survey’s respondents consider them as a critical part of IT infrastructure. Nowadays, a third of organizations are managing 10 to 99 firewalls and for a quarter of the organizations, the number is above 100, though these usually differ by manufacturers and models.
Firewall management can become time-consuming not only because of their increase in number but also because, - like most the other security elements - they are not completely autonomous. To fulfil its purpose to protect against unauthorised access, firewalls must be managed properly without faulty policy configuration. Nevertheless, as much as 40 % of respondents make 10 to 99 changes in firewall policies per week.
Another problem is that configured changes are usually done by network administrators (as the firewall is a network element) and not by security specialists. Often though, they are not coordinated and change rules based on the requirements for services availability, which wouldn't have to meet the cybersecurity and information security requirements. They also don’t disable the out-of-date rulesets often or create faulty ones by mistake.
It is not surprising that this leads to misconfigurations and vulnerabilities, which impact security operations and are often a vector for cybersecurity incidents.
Yes for Audit but not One-Off
Multiple organizations’ answer on these problems is firewall policy auditing. It is not a banal thing, that’s why most organizations do it manually only once a year.
During the audit, it is essential to gather large amounts of information and create a review of settings, rulesets, and firewall access logs. Naturally, when evaluating and comparing with internal policies and rulesets, it is important to identify all the risks and make sure not to deny access to apps and data to legitimate users. Consequently, it is necessary to create the Change Management process and oversee its realization.
Whoever can manage to overcome this difficult process should make sure of the continuous monitoring, update settings in accordance with changing policies, terms, and conditions such as prompt access to chosen apps and data to employees, who happened to work from home.
Automation is the solution
It is evident that with the increased number of configured policies and rulesets, its management and control become too complicated and non-effective if not completely absurd.
The solution is to automate control of the firewall's policy accuracy. Specialized tools, such as Synapsa Auditor can be used as it continuously checks the accuracy of the configured policies setting and security rulesets in real-time.
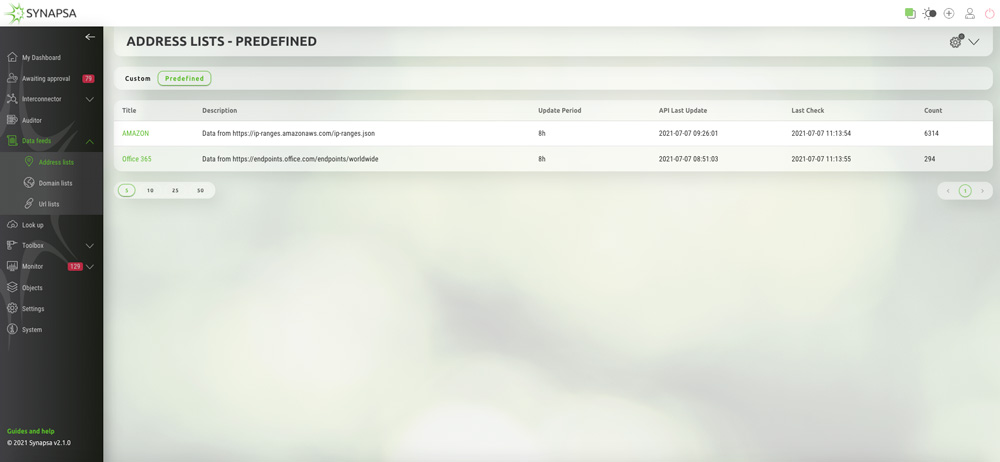
Combined with the predefined and custom IP, domain, and URL lists in Synapsa Data Feeds, it is possible to use effective Content Delivery Network (CDN) with the help of the external dynamic lists (EDL) for SaaS and cloud services without the need to constantly change and update rulesets on firewalls manually.
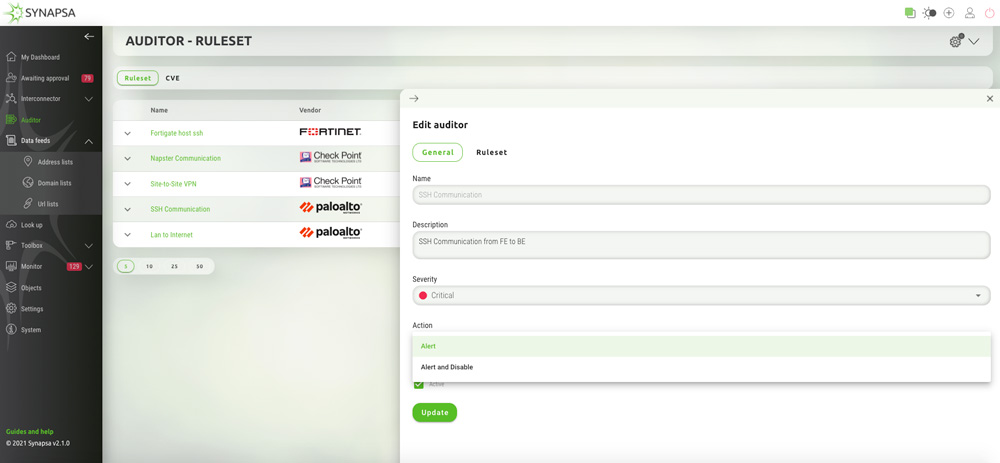
How does it work?
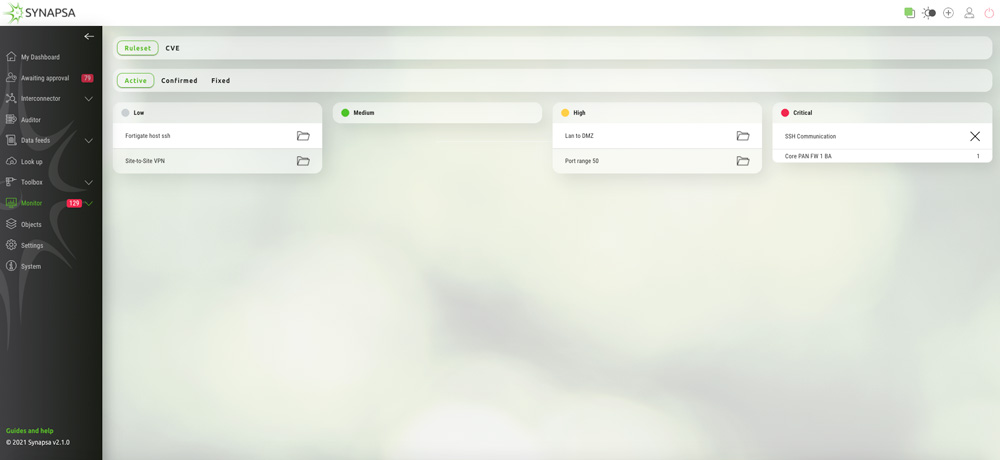
Auditor compares continuously current firewall policies configuration thanks to predefined rulesets directly in Synapsa Platform, identifies faulty and out-of-date ones that are not in security compliance, and alerts departments responsible for Network and Security Operation automatically and in real-time which contributes to better coordination.
It mostly allows the Security Operation based on these rulesets severity and their automated or semi-automated option to disable firewall faulty policies without the permission for its configuration.
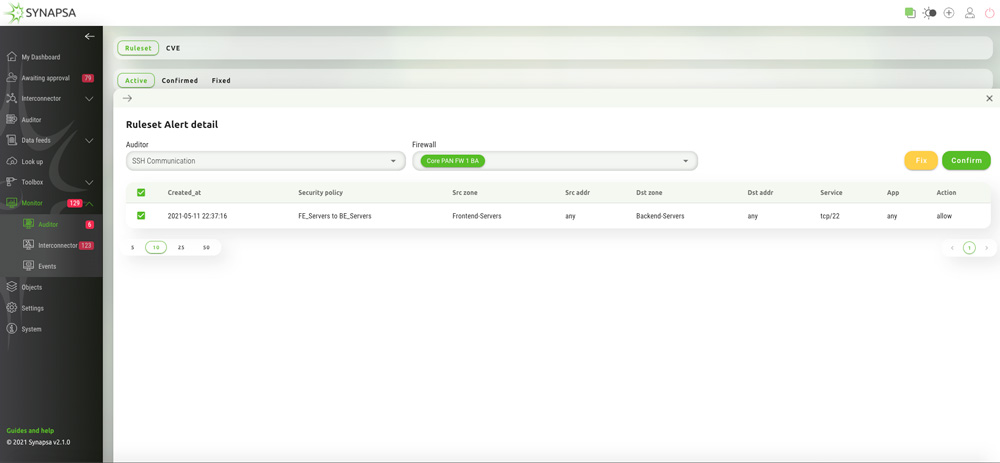
It immediately sends notifications to responsible administrators, to the Security Information Event Management (SIEM) system or Security Orchestration, Automation and Response platforms (SOAR) about these automated activities. Auditor also continually checks the vulnerabilities (CVEs), occurring on firewalls.
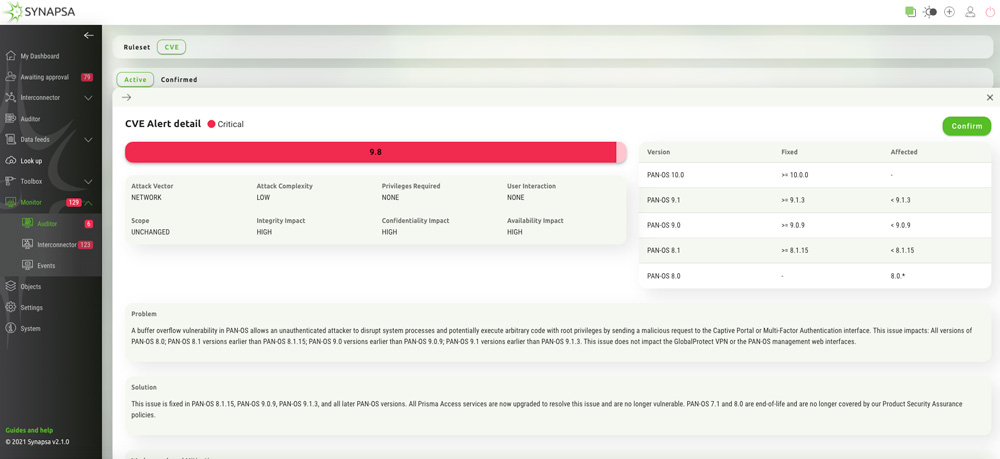
Above all, this results in a simple and automated resolving of weak spots in securing the network but also many other benefits.
For example, the system provides proof for possible regulator investigation or to the stakeholders that all security policies and rulesets have been set and adhered to and possibly when and what had been changed. Finally, it also improves coordination and increases the productivity of network admins and security specialists, reduces the time needed for changing demands and minimizes the risk of cybersecurity incidents in real-time.
Summary
The same that applies to the whole IT security applies to firewalls- adequate security is not the product, but a continuous process. Synapsa Platform brings automated solutions for Firewall Policy Auditing (FPA) and simplifies activities in Security Policy Change Management (SPCM) and Security Policy Audit and Enforcement (SPAE).





