Why do we automate Incident Response?

Automation is the key aspect in cyber threats mitigation
IT security specialists and SecOps departments responsible for cyber security have been under enormous pressure over the past year. Though, it is not only because of the pandemic, which shifted a huge proportion of our lives online. The situation has also worsened due to more effective tools with AI components, which allow for attacks to be automated and pass through the cyber protection more easily.
Huge differences
More than half of business managers acknowledge that security strategies based on people’s responses cannot respond to dynamics of cyber-attacks as stated by MIT Technology Review in this January’s global survey.
This means that responses to detrimental events and attacks either become delayed or next to none. The response is usually sparked only after there has already been a data breach or compromised infrastructure. According to CrowdStrike research, it took on average 79 days for the organisations to identify an attacker's access into the compromised infrastructure in 2020.
What’s striking is the huge differences in organisations’ abilities to identify and respond to cyber incidents on time. Although the average is 79 days, in practise, while it takes only hours or days to identify these incidents in some organisations, it can take up to 6 months for others.
These significant differences also occur with ransomware attacks. While the average timeframe from detection to mitigation was 45 days last year, more than a quarter of organisations were able to respond within a day and 48 % within a week. Though, failure to mitigate near real time can have fatal consequences.
Overburden and data flooding
Quick responsiveness to various security incidents is a key metric of an effective team or SecOps department responsible for IT security. However, to achieve a high score based on the criteria is almost impossible without adequate tools.
Many organisations are gradually introducing automated systems into their toolbox, such as EDR (Endpoint Detection and Response), NDR (Network Detection and Response) or even XDR (Extended Detection and Response) so are able to process more effective logs into SIEM (Security Information and Event Management) systems. It is the increase in information noise that causes security operators and analysts to be overloaded and if response automation is missing when sorting and evaluating the events, the effectiveness of these technologies can drastically decrease.
Stats show that security specialists spend nowadays around half a time resolving different events in 3/4 of organisations and in 1/3 of organisations, the 80 % of work time is dedicated towards cyber events.
The result of delayed or insufficient response to various seemingly insignificant events in a network environment that allow attackers comfortable and smooth access to infrastructure, results in serious incidents in terms of data breach and consequently asking for a ransom.
The key to effectiveness

Detection

Automation

Response
How can organisations ensure timely and consistent response to anomalies or suspicious events in networks behind which can be a sophisticated attack? This can be only when the organisation is not only able to detect, triage and evaluate using automation, but to also mitigate and respond with automation, thanks to which the unauthorised access to infrastructure and systems or ‘lateral movement’ can be blocked even before the attacker causes any extensive damages.
For example, it could be automatically blocking suspicious communication in the network in real time based on the alerts from EDR, NDR, XDR or SIEM, or to perform any other actions such as blocking an anomalous activities which could be used by an adversary to exploitation and command and control procedures.
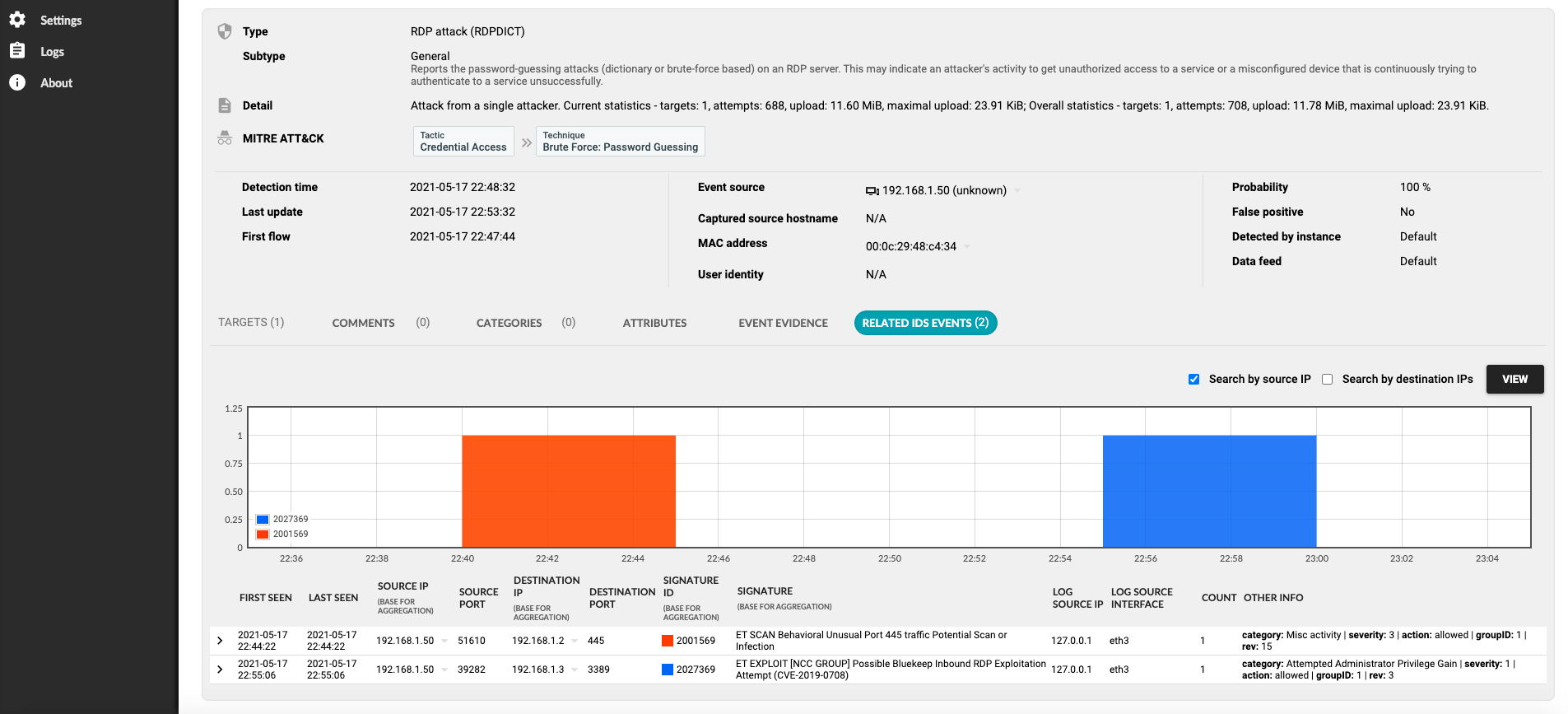
Solution
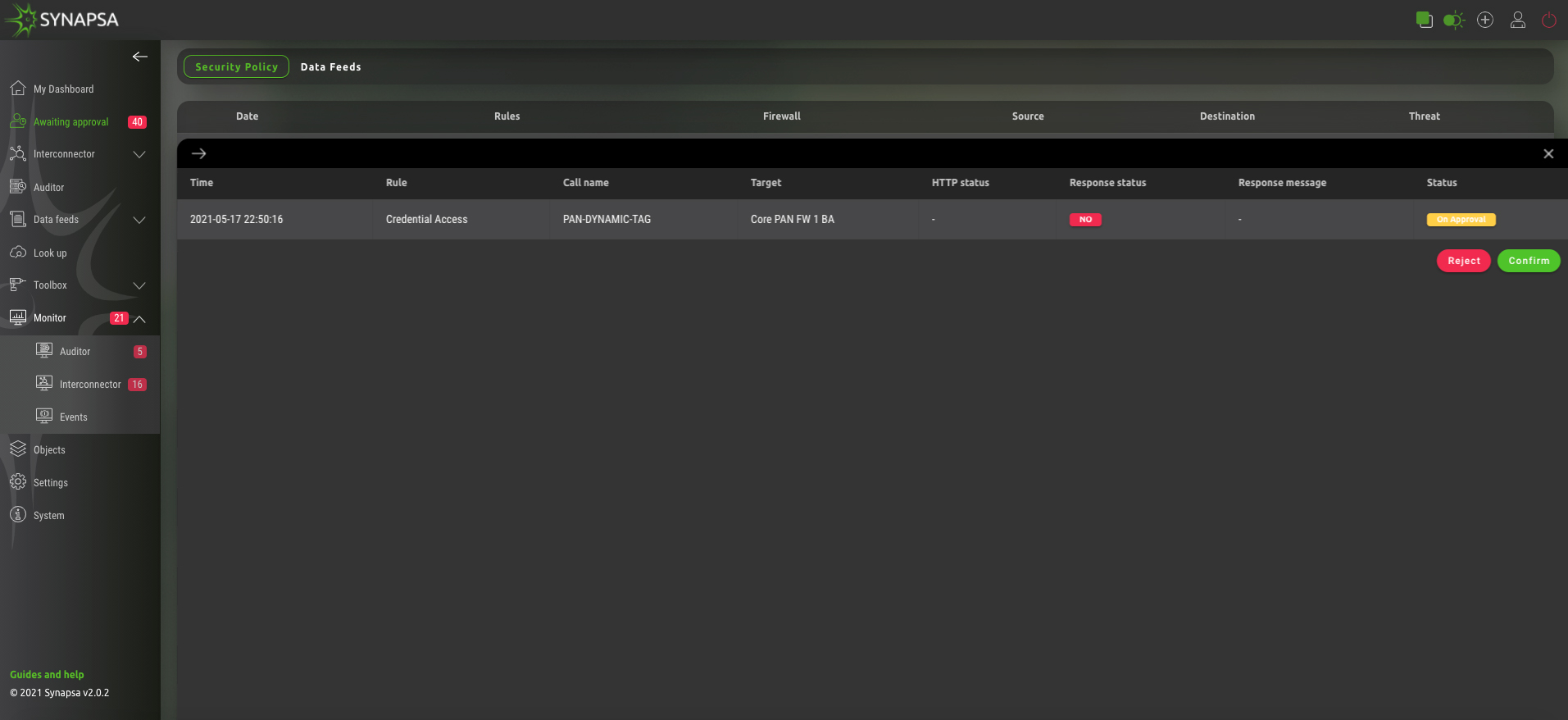
Synapsa Platform presents a simple and intuitive docker based API client, which thanks to the Interconnector module allows security operators and specialists to perform automated malicious communications blocking, anomalous behaviour isolating and cyber-attacks mitigation in real time. All thanks to providing API based interconnection between various devices and tools in infrastructure. Moreover, there is no need for manual configuration of rulesets in interconnected assets and infrastructure devices on which specialists usually do not have permission.
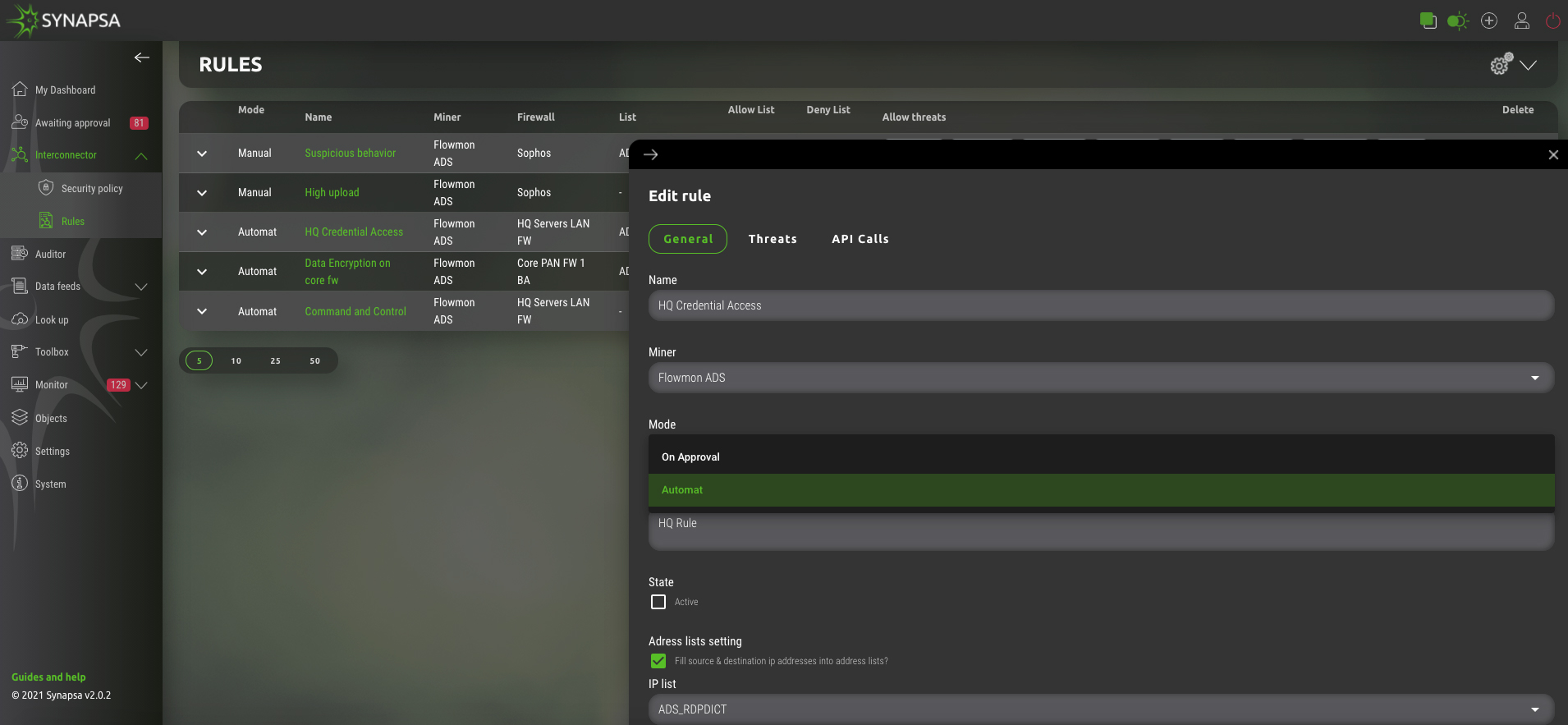
Interconnector allows to create configuration or security rulesets and at the same time update these rulesets with updated information, which are changed in time, without the need of committing it (such as on firewalls).
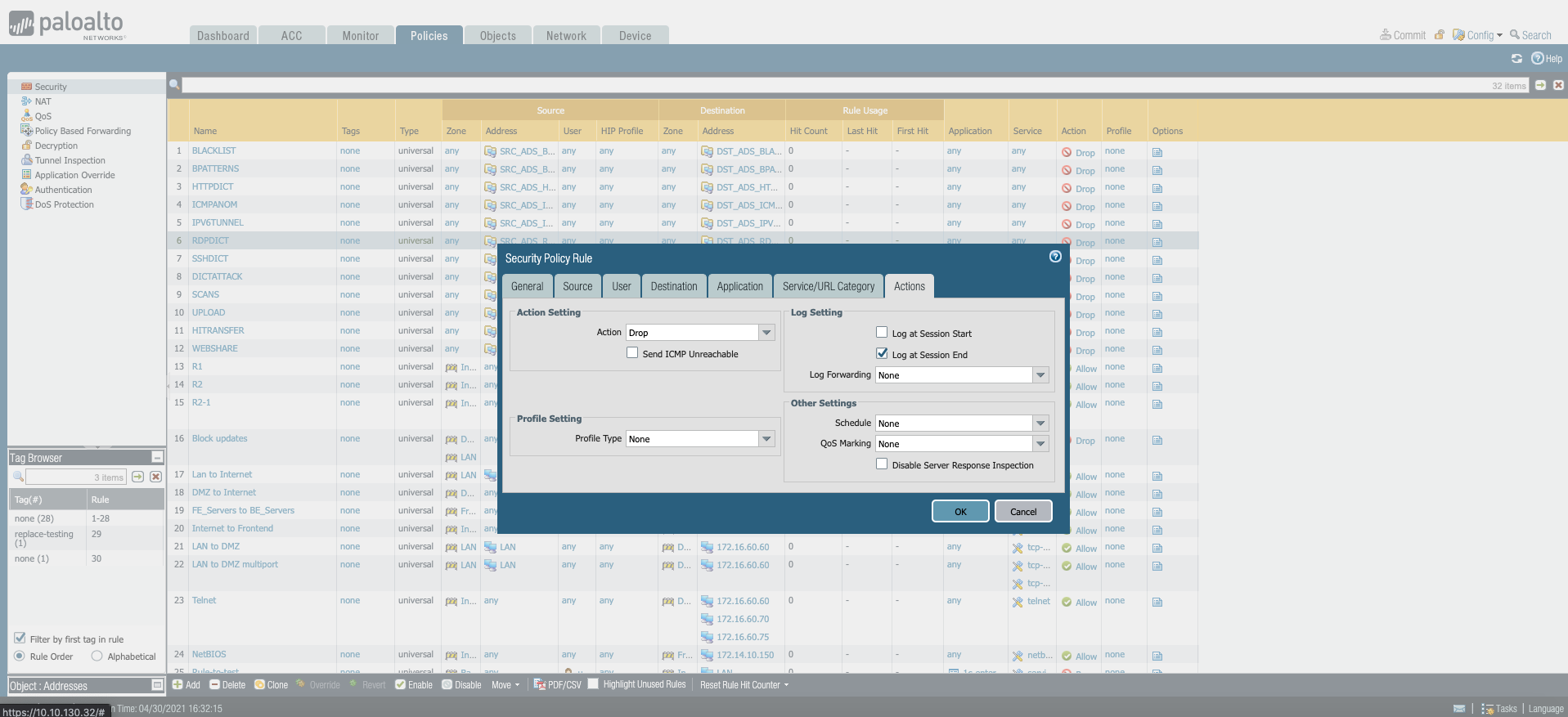
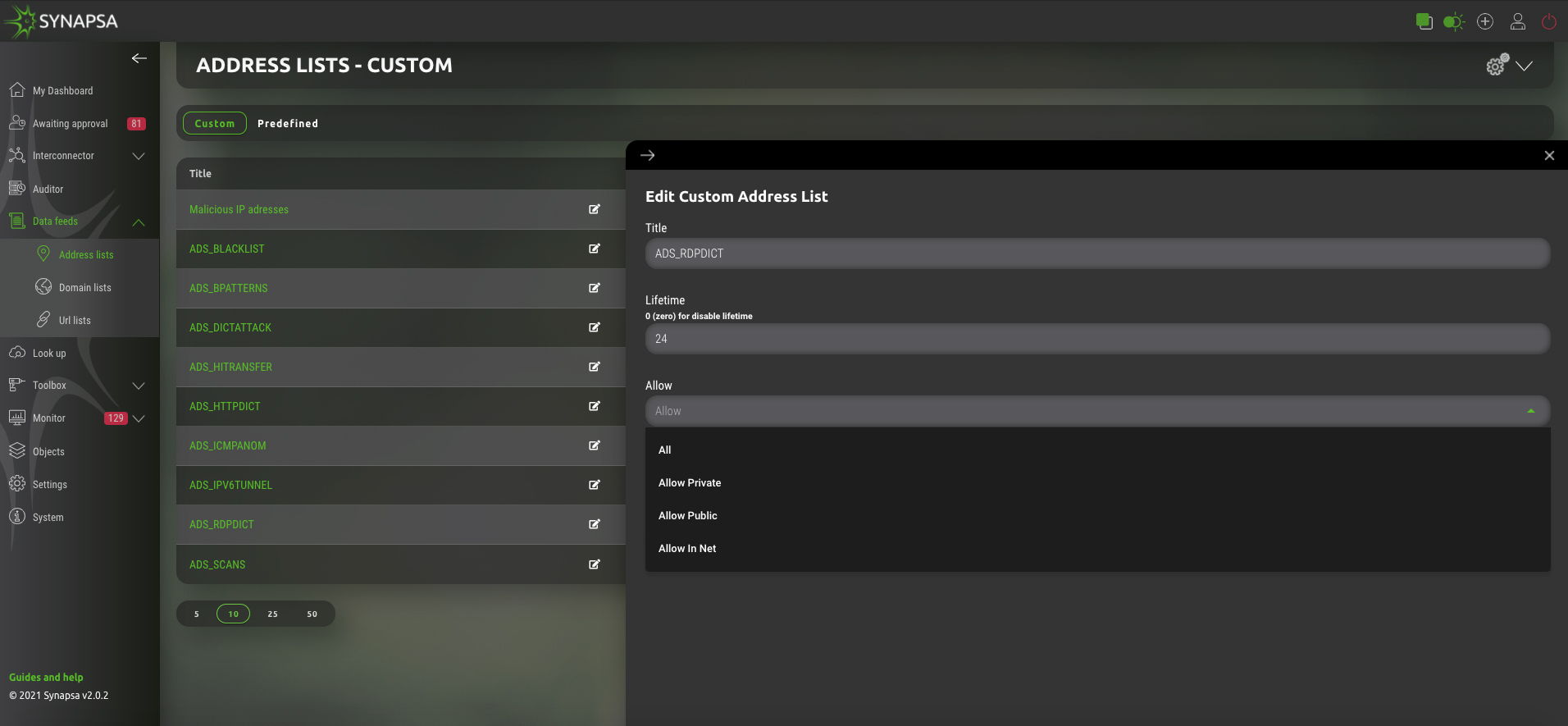
Moreover, at constant data collection in terms of the Data Feeds module, it will fully automate CDN (Content Delivery Network) or enrich configuration or security rulesets on individual devices by using EDL (External Dynamic List).
Of course, similar interventions can have a negative impact on users’ comfort and satisfaction, since it can also affect legitimate activities in the network to some extent. This is why some responses within the mitigation process can be semi-automated, allowing security specialists to decide after being notified, about the next step in just one click.
Summary
Automation makes work easier and shortens security Incident Response time, as agreed by 88 % respondents in Exabeam survey. As a result, increased response time significantly reduces potential damages. Consequently, this is why using automated or semi-automated mitigation processes is essential and no effective team responsible for security operations can do without it.





