 Synapsa Auditor
Synapsa Auditor
Synapsa Auditor allows operators to have complete control over the configuration and compliance with your standards or any industry benchmark.
 Synapsa Auditor
Synapsa Auditor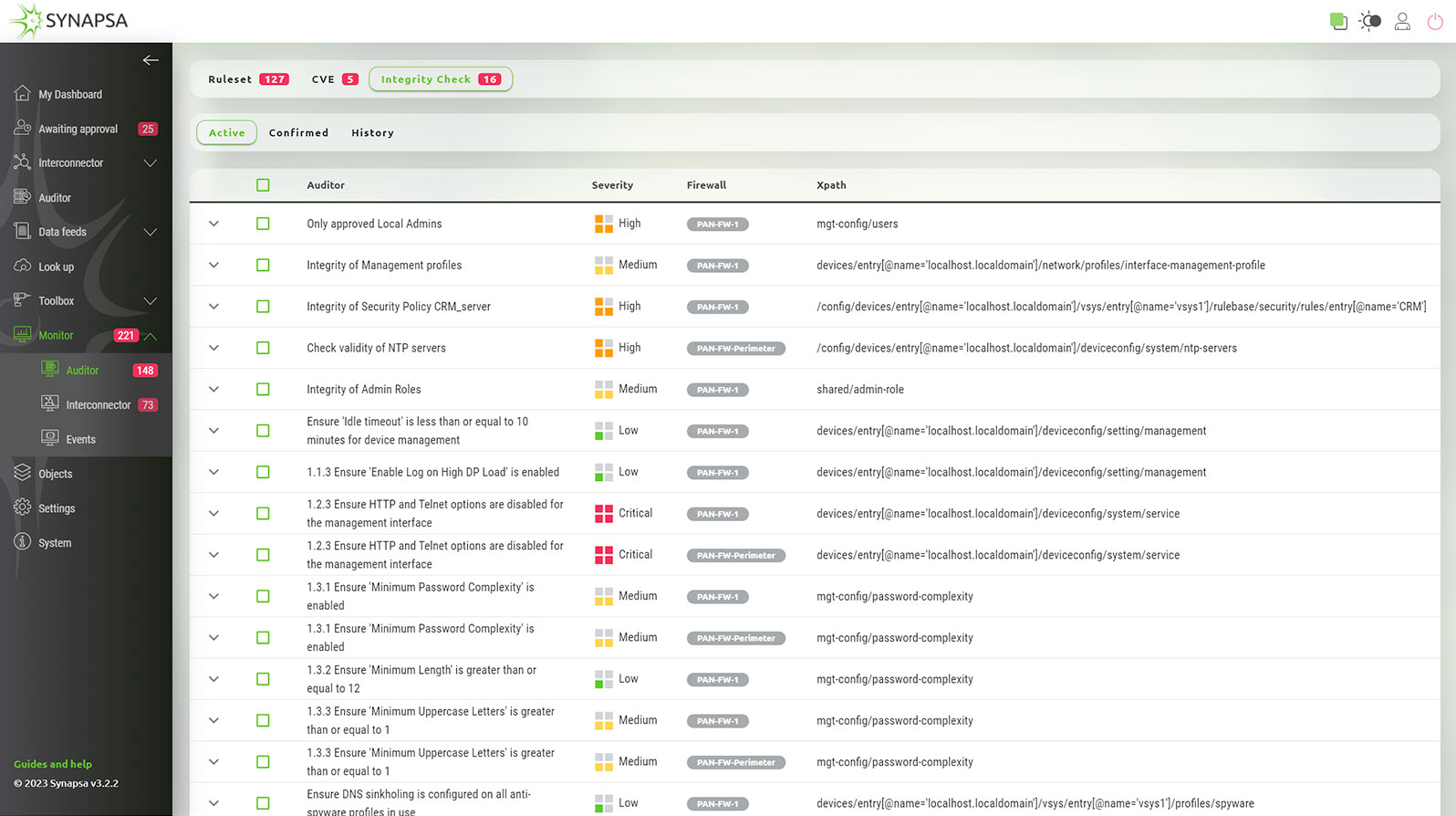
The “allow and forget” approach is not secure. There is a need to constantly monitor the integrity of the configuration and to make sure there is no hidden, forgotten or even purposely configured part, which could make you vulnerable.
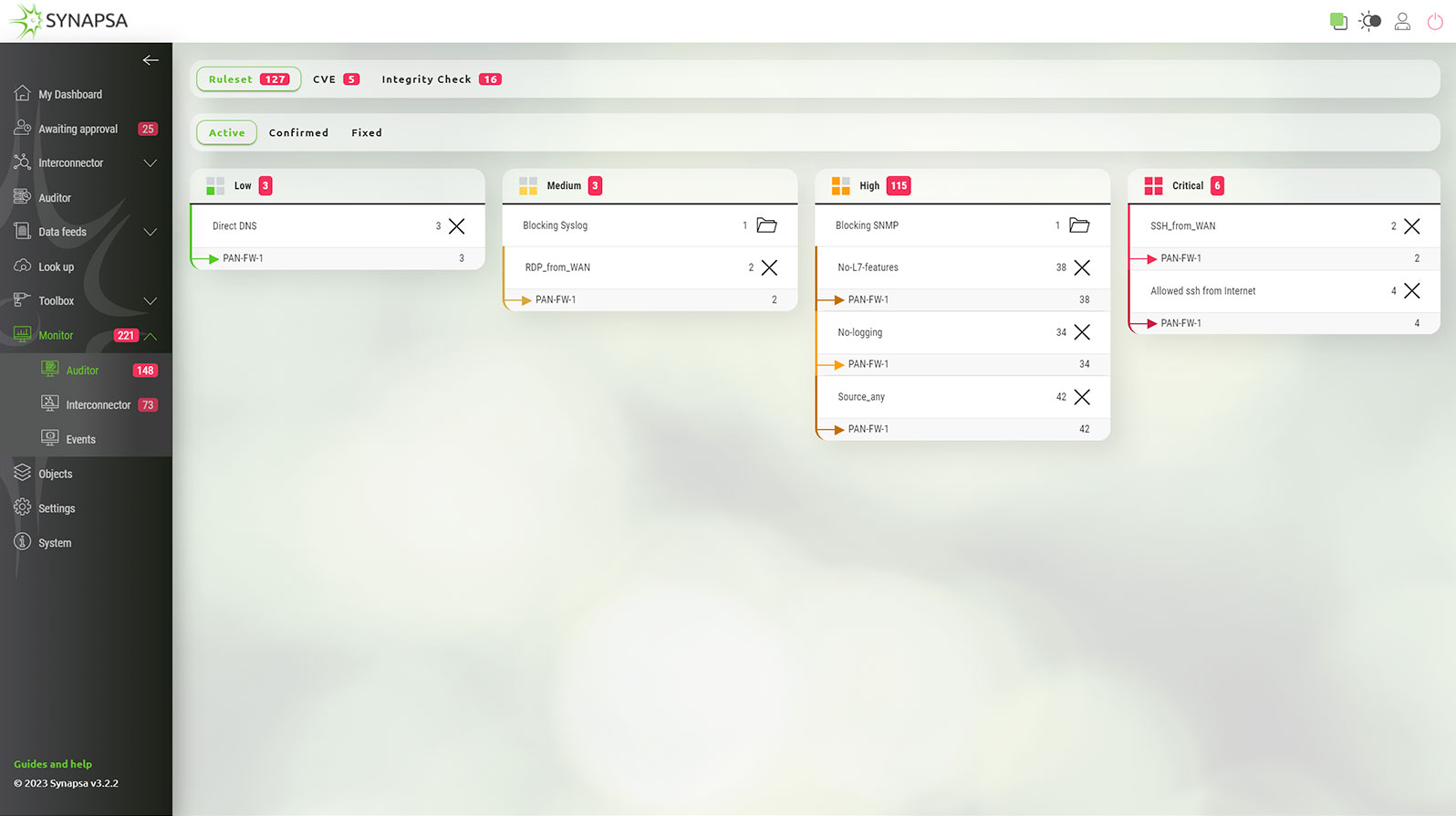
Synapsa Auditor calculates overall security score over all the monitored devices, keeping the complete history and showing the timeline of exposure in the dashboards. Security engineers can easily identify when the score increased due to the misconfiguration or wrongly implemented security policy.
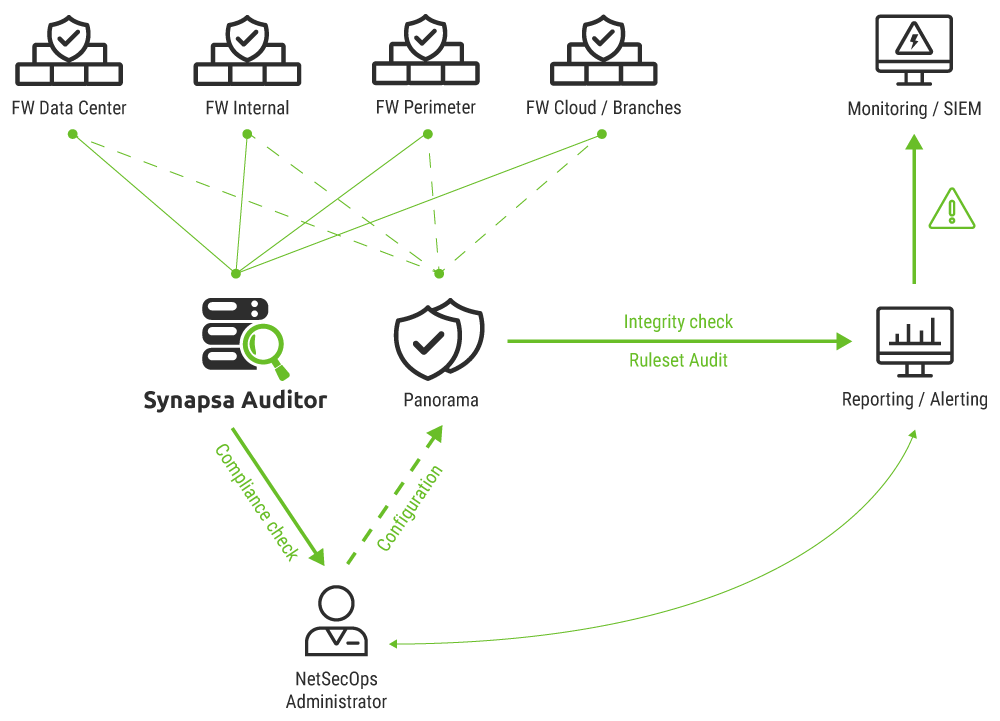
Note: Panorama is not needed, Synapsa is connecting directly to firewalls and checking effective configuration.

Synapsa Auditor is capable of real-time audit over your security rulebase, making sure that there are no misconfigurations, dangerous rules, widely open policies or that you are not blocking any critical traffic such as management or monitoring.

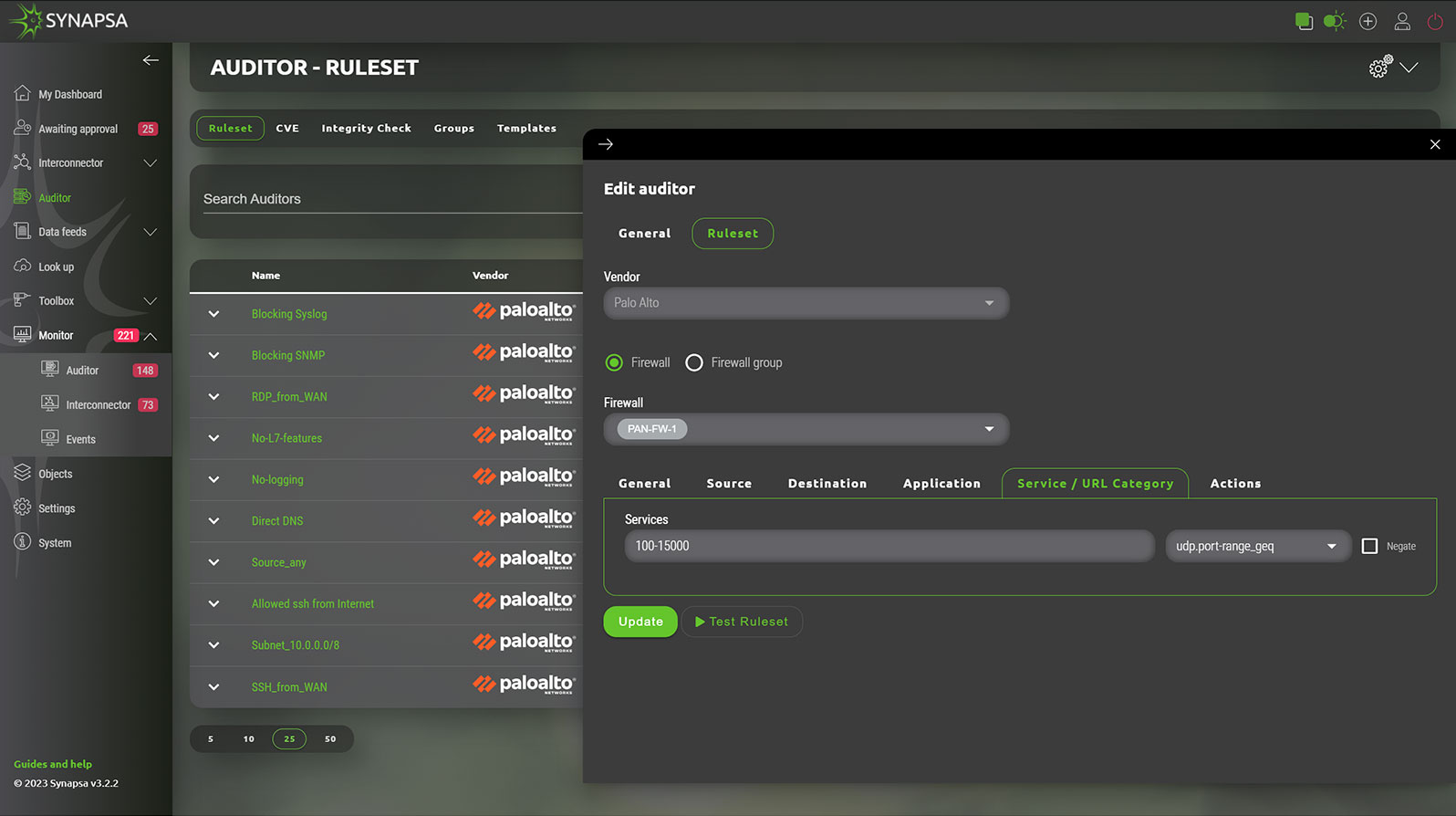
Synapsa Auditor allows operators to guard literally any part of the configuration, whether it's matching corporate approved standards, and if there is no malicious config item or parameter which opens doors to the organization. It allows checking the CIS Benchmark requirements in real-time and without hassle.
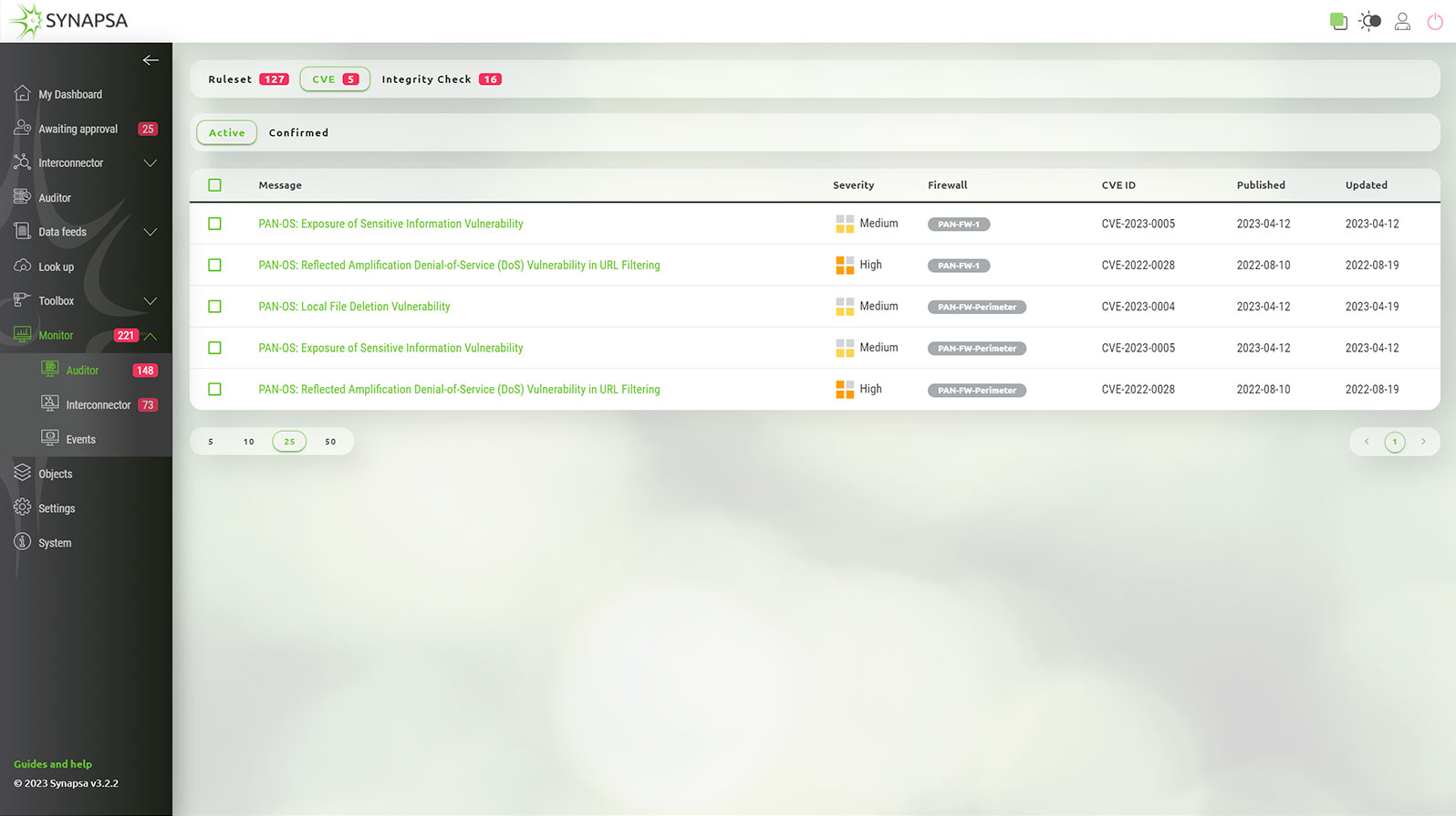
Synapsa Auditor constantly monitors the current operating system running on firewalls and other network assets using the official vendor security advisories, which provides accurate and up to date information about the vulnerabilities you are facing. There is complete information about the severity of the vulnerability, how to fix it or apply possible workaround, just one click away.
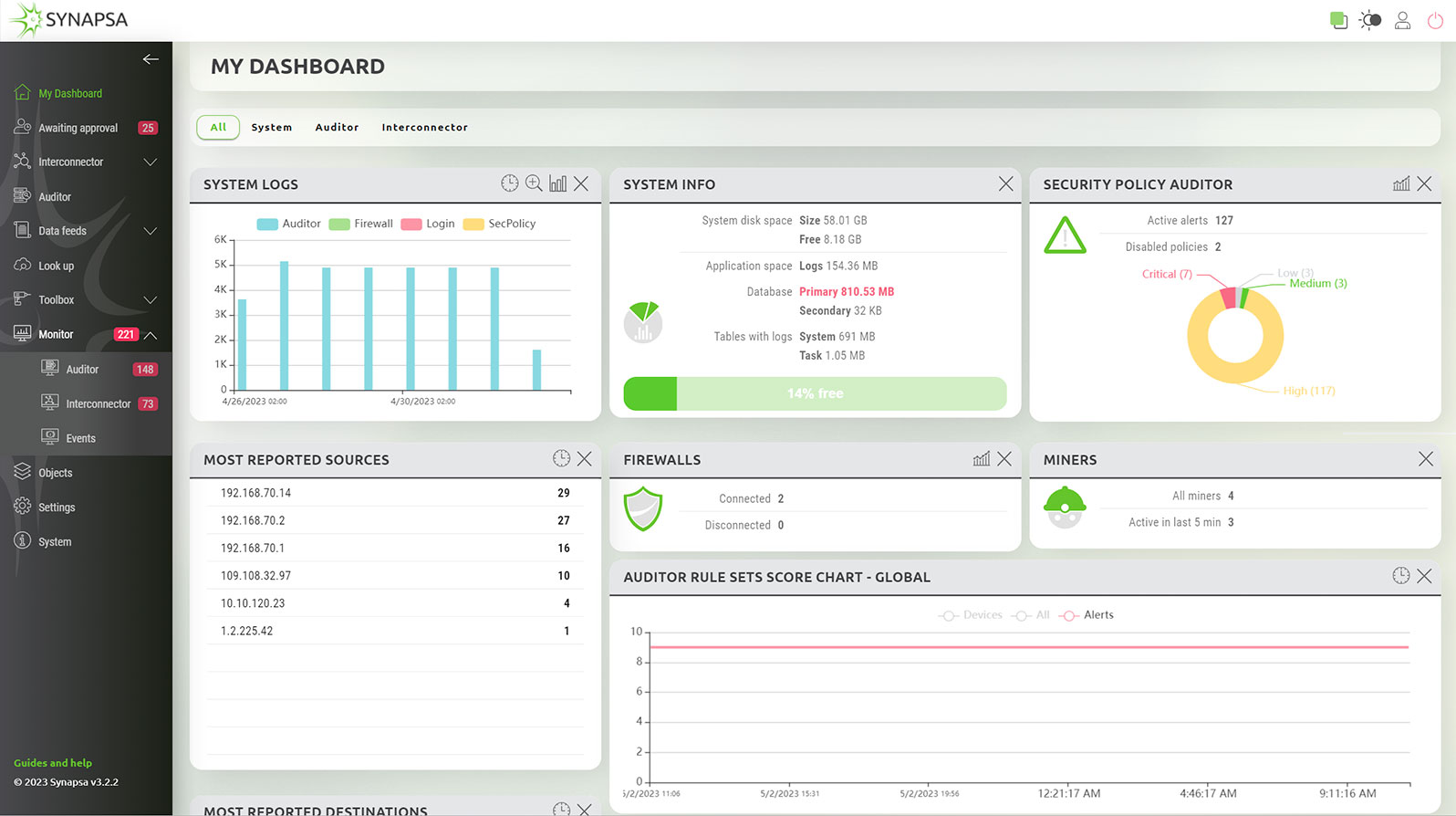
You get a complete overview of the current compliance status in the dashboard widgets, either aggregated for all the monitored devices, or individually for each asset. Synapsa Auditor exports the findings to 3rd party monitoring and management tools, and is able to automatically fix violations to the security policy. Security or network operators can easily spot when exactly a violation has occurred, which device caused it, and take immediate action without leaving the organization vulnerable to exploits.



© 2024 Synapsa Networks
designed by illusmart
This website use cookies and analytical data. In case you agree with that please click on the "I agree" button bellow. Details can be found on a page Information for the processing of personal data.