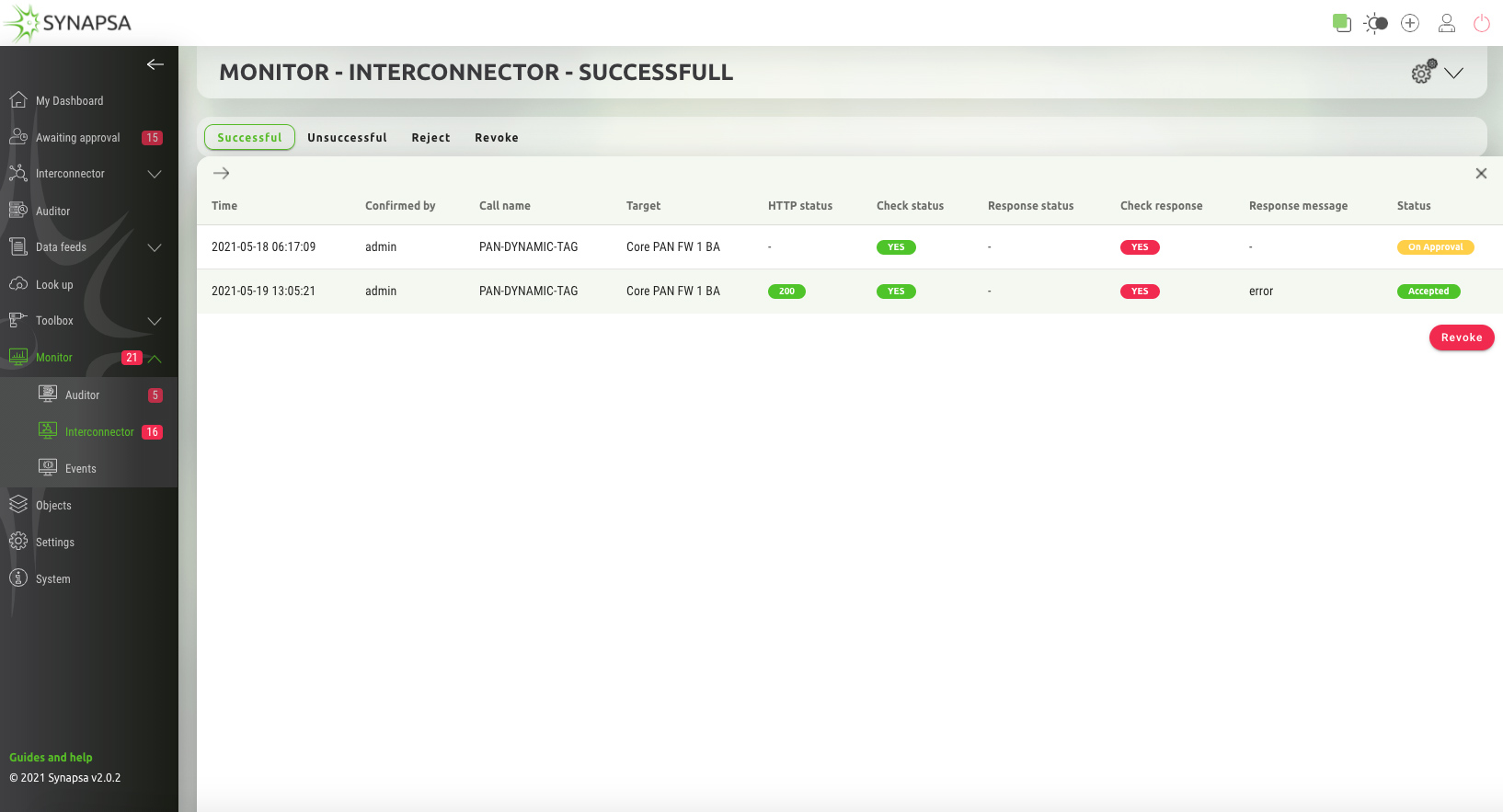
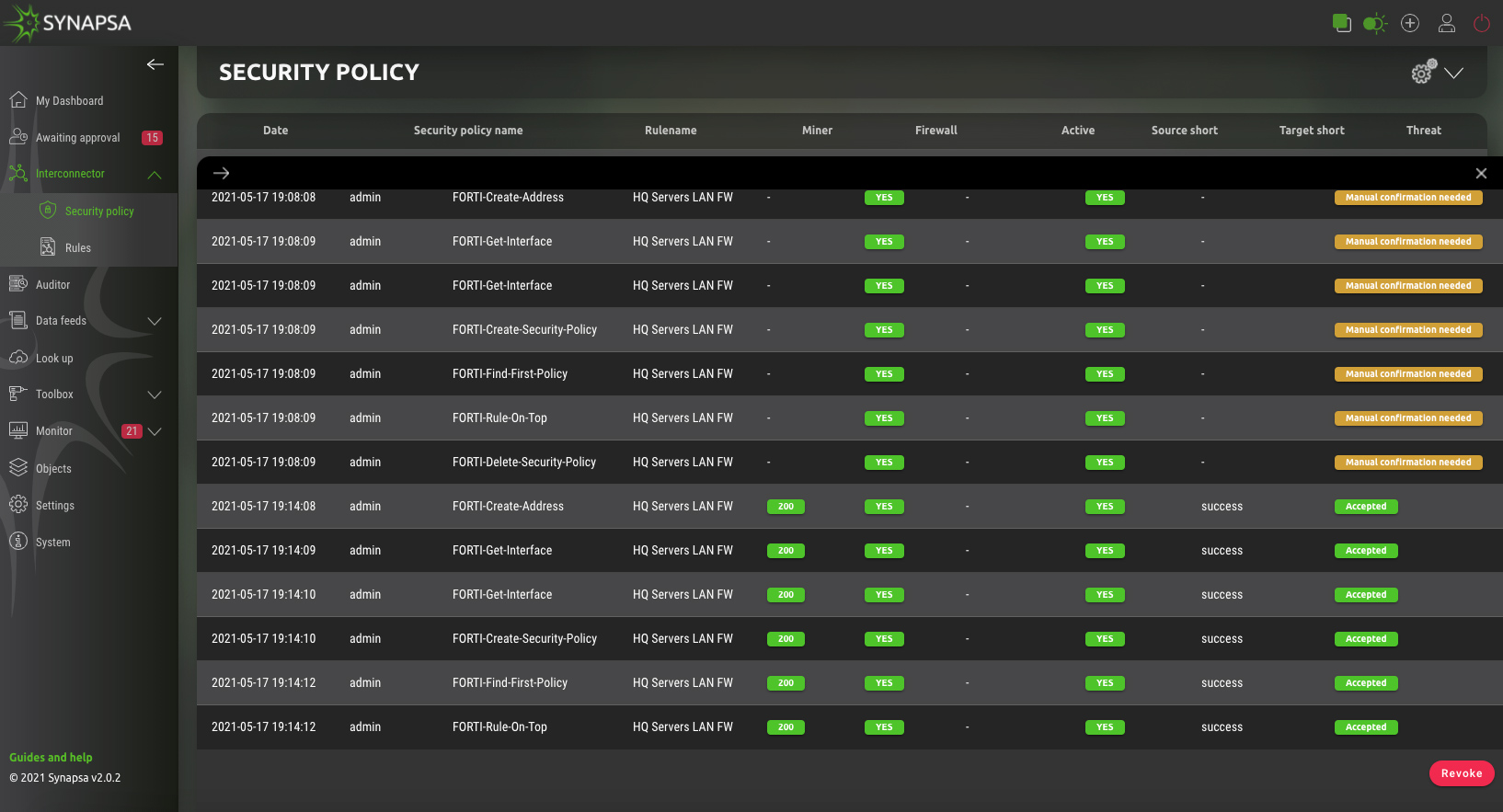
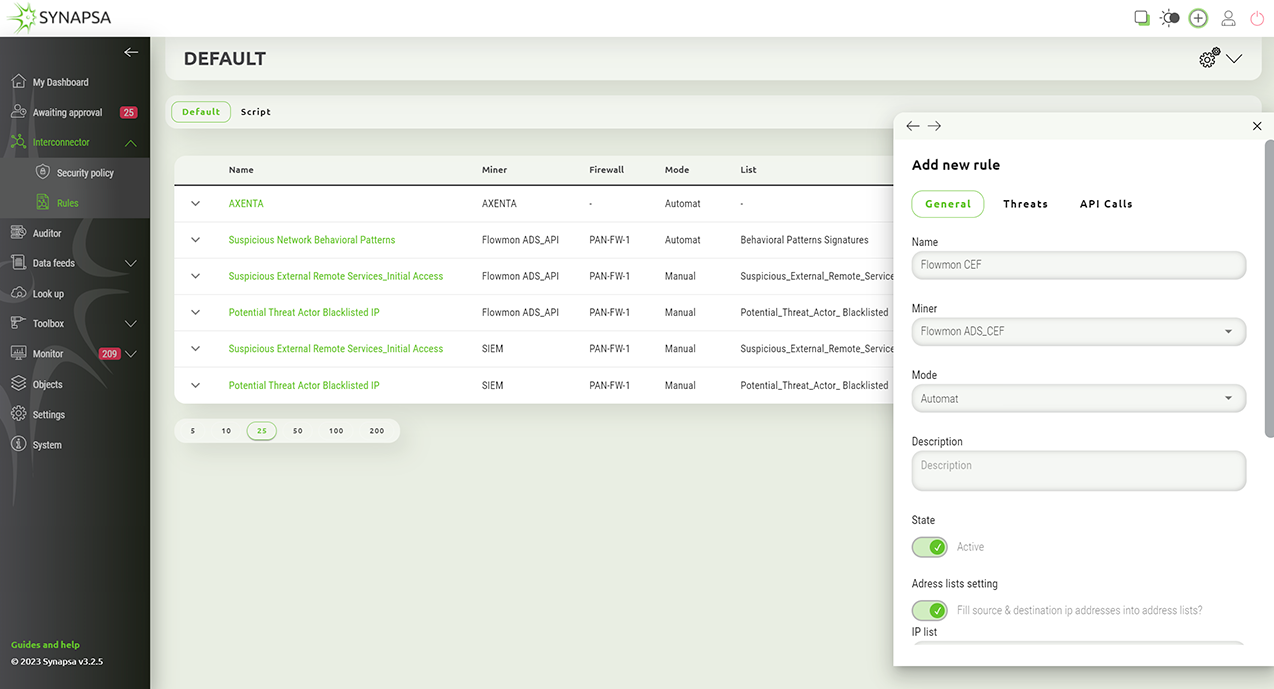
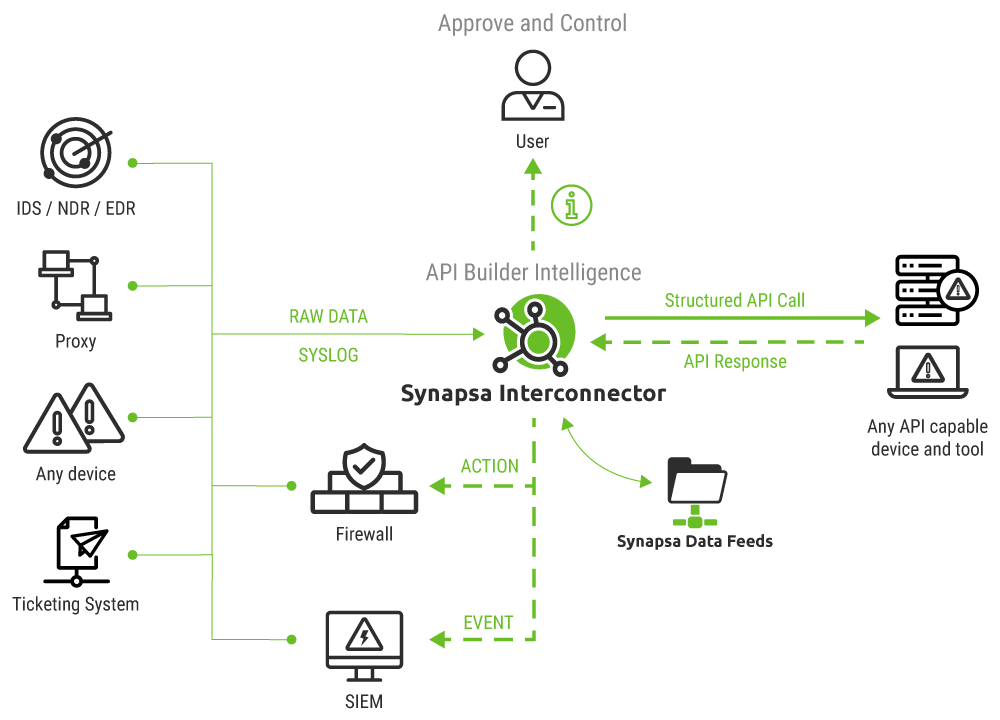
Synapsa Interconnector
Synapsa Interconnector
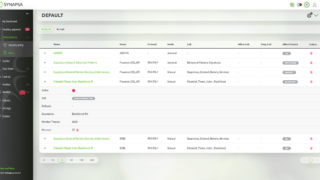
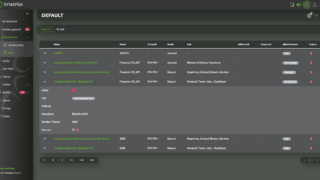
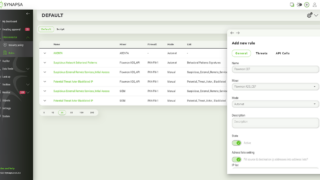
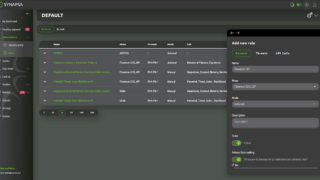
Automatically processes input data from any source (miner) capable of sending syslog such as SIEM, Firewalls, Proxy, Servers and other endpoints. By leveraging the built-in parsers it is possible to extract any data and reuse it in various automation tasks.