Operation security budgets on the rise
Automation should not be left out
IT security departments have never had it tougher. This is because any number of systems failures and service outage can leave a more significant impact on organisations than in the past. On the other hand, ensuring smooth traffic in ever complicated IT environment is exceedingly difficult.
To protect against data misuse and system outage, the specialists use more intense multiple monitoring systems. In bigger organisations, this could be dozens of appliances watching after different IT infrastructure parts and together producing information flow.
For instance, according to the IDG Research Survey, some participants stated on average
14 300 daily alerts, from which two thirds reported daily alerts increase during the past 12 months, prior to filling the survey.
Only a small portion are irrelevant alerts caused by hardware of software infrastructure changes.
Even after filtrating these alerts, the specialists still have to analyse and react to tens or hundreds of incidents notifications. To investigate and solve even one of these, classified as important, could take approximately 12 hours.
What troubles the specialists
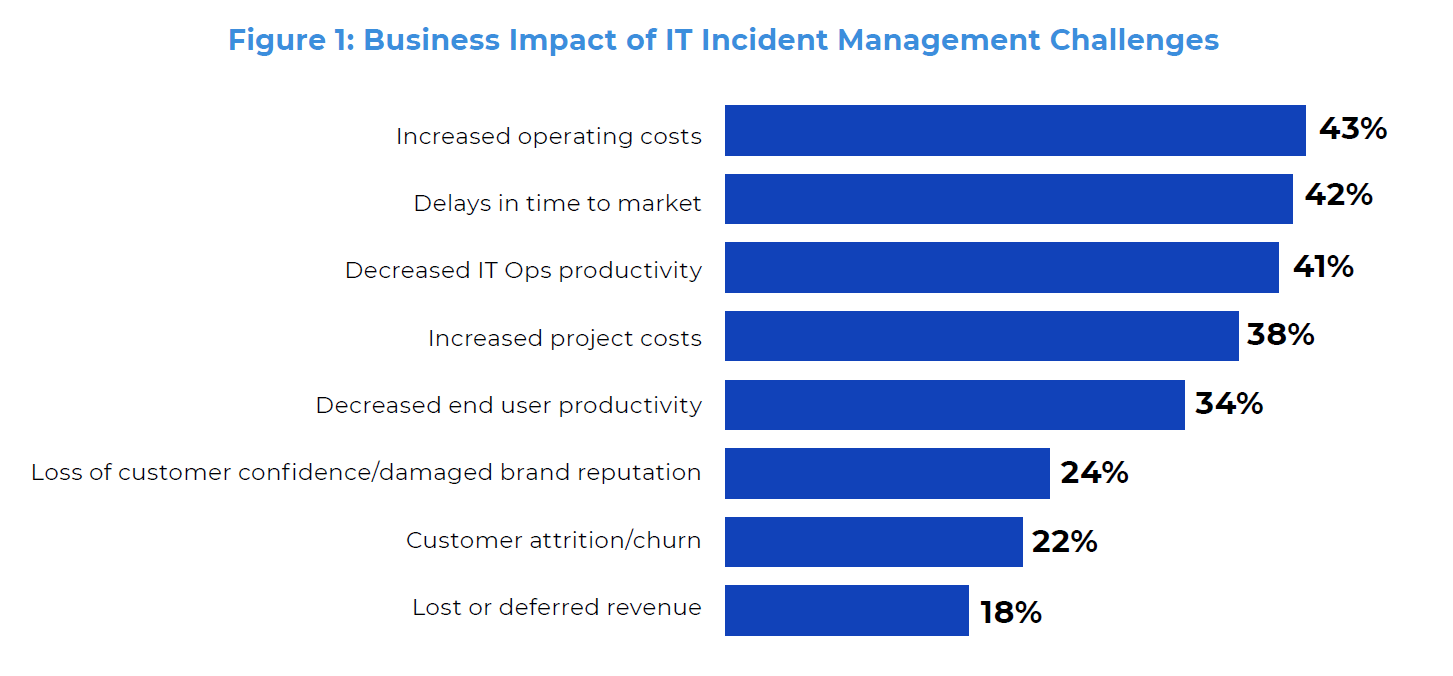
According to IDG survey, IT departments face various challenges regarding Incident Management. Among the most important are coordination across responsible teams or persons (47 %), availability of suitable knowledge and skills (45 %) as well as information noise and overload (36 %).
Moreover, these studies have summarised that this leads to increased operating costs, decreased IT security specialists, end user’s productivity and increased in customer dissatisfaction.
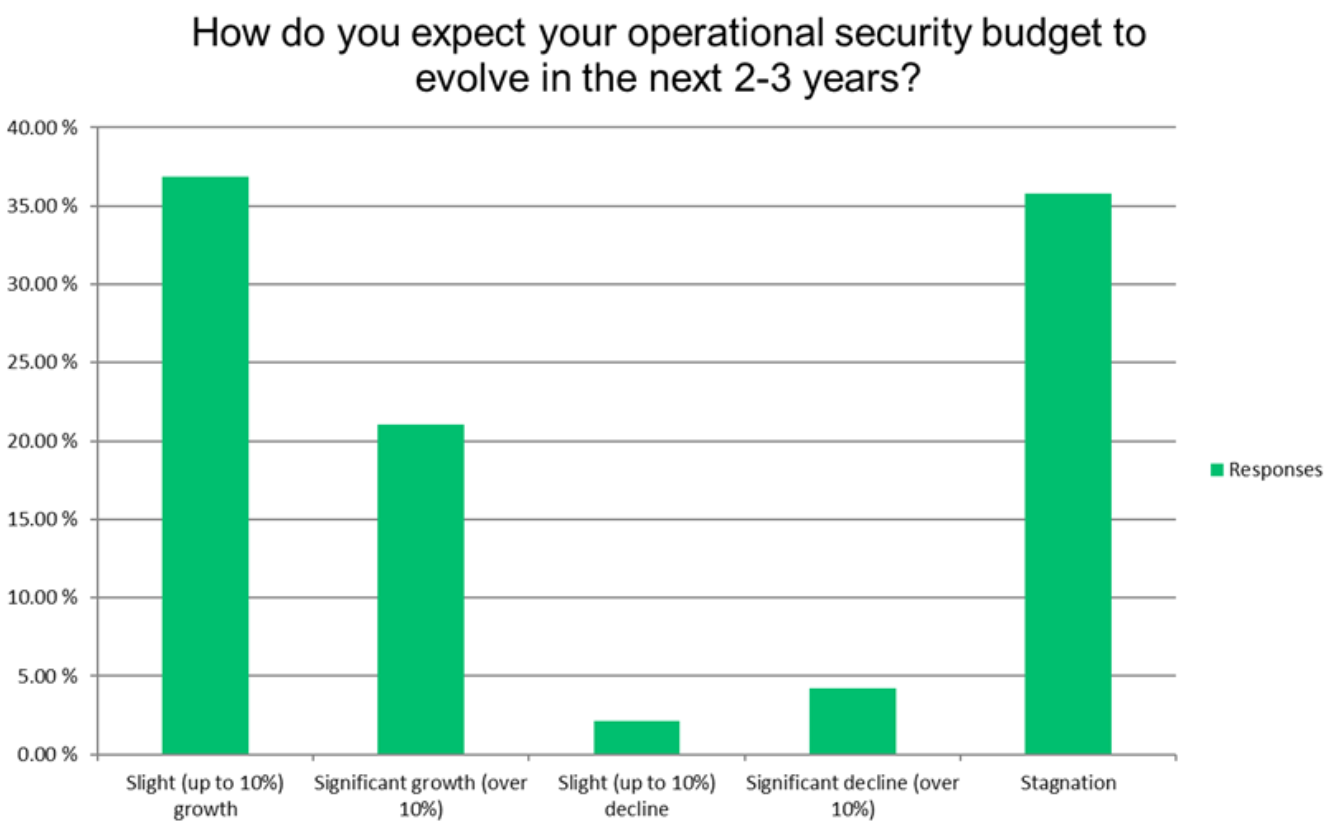
The challenges facing SecOps teams also reflect in operational security budgets. In the next two or three years, most organisations are planning to increase their budgets; and one fifth is expecting the increase of more than 10 %.
Investment in automation
Based on the above-described IT security teams challenges, it is inevitable, in terms of the increased budget, to invest in automation tools, which connect cyber threat detection and subsequent reaction to security incidents.
In practise, these tools can automatically block or isolate suspicious communication and interactions with command-and-control servers after detection, or to independently undertake various necessary steps at confirmed malware infection, such as to turn off infected system network connection and to identify other vulnerable IT infrastructure parts. This could protect data when infected with ransomware, especially when the organisation does not have 24 hours IT infrastructure monitoring in place.
Apart from this, these tools can also bring other advantages, like helping to control agreements with organizational security rules and apply them without human resources utilisation.



